Some VaultPress plans include daily security scanning, and our most advanced subscription includes one-click threat resolution. On this page, you’ll learn about some common threats and how to address them. If you have any questions, drop us a line.
Managing Threats
For security threats, you will see the following three options:
- Repair Threat: Click this to fix the threat! Please note that not all threats will have this option. This button will only be available for supported plans
- Ignore Threat: Click this to ignore the threat. Only do so if you have contacted us to confirm it’s a false alarm or you are sure that the threat has been addressed
- File Affected: Click this to see more information about the suspicious file
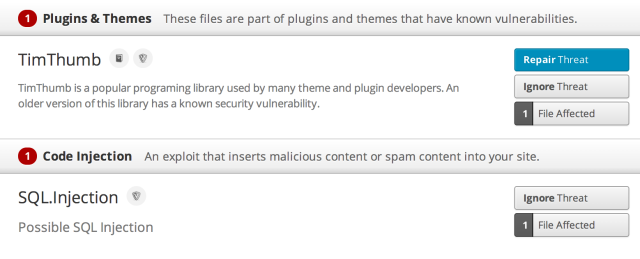
Below is an example of what two different security threats look like and how the options are displayed for each:
Under some threats, you might see next steps for you to take. An example of this might be to upgrade the plugin. If you do not see these next steps, don’t worry – that just means to contact us – we’ll point you in the right direction.
Changes to Core WordPress Files
VaultPress checks your WordPress installation to see if any core files have been changed or deleted. Generally, these files should never be changed. WordPress functionality should be altered by using plugins and themes instead.
If you didn’t make the changes to your core files, you should consider the files suspicious, and replace them by reinstalling your WordPress core or having your host do so.
Web-Based Shells
Web-based shells give an attacker full access to your server, allowing them to execute malicious code, delete files, make changes to your database, and more.
Shells are usually found in files, and can be removed by cleaning the added code from the file or deleting the file altogether from your server. You can then replace it with a clean version from your backup.
TimThumb Vulnerability
TimThumb was a popular script that allows users to resize images on the fly. Since it was sometimes present within themes and plugins, you might not have even known you were running it.
Older versions of TimThumb included vulnerabilities that allows third parties to upload and execute malicious code in the TimThumb cache directory.
TimThumb is no longer being supported or maintained, and if you have a theme that still uses it, you should consider a newer, more modern theme that doesn’t rely on it.
If you have any questions about security threats or suspicious code, you’re always welcome to contact us.